Master Palo Alto Networks PCNSA Exam with Reliable Practice Questions
An administrator wants to reference the same address object in Security policies on 100 Panorama managed firewalls, across 10 device groups and five templates.
Which configuration action should the administrator take when creating the address object?
Correct : A
To reference the same address object in Security policies on 100 Panorama-managed firewalls, across 10 device groups and five templates, the administrator should ensure that the Shared option is checked when creating the address object. This option allows the administrator to create a shared address object that is available to all device groups and templates on Panorama.The shared address object can then be used in multiple firewall policy rules, filters, and other functions1.This reduces the complexity and duplication of managing address objects across multiple firewalls2.Reference:Address Objects,Create a Shared Address Object,Certifications - Palo Alto Networks,Palo Alto Networks Certified Network Security Administrator (PAN-OS 10.0)or [Palo Alto Networks Certified Network Security Administrator (PAN-OS 10.0)].
Start a Discussions
What are three configurable interface types for a data-plane ethernet interface? (Choose three.)
Correct : A, C, D
Three configurable interface types for a data-plane ethernet interface are Layer 3, VWire, and Layer 2. These interface types determine how the firewall processes traffic and applies security policies. Some of the characteristics of these interface types are:
Layer 3: A layer 3 interface allows the firewall to act as a router and participate in the network routing.The firewall can send and receive traffic from a layer 3 interface and apply security policies and inspect the traffic based on the source and destination IP addresses and zones of the interface1.
VWire: A virtual wire interface allows the firewall to transparently pass traffic between two network segments without modifying the packets or affecting the routing.The firewall can still apply security policies and inspect the traffic based on the source and destination zones of the virtual wire2.
Layer 2: A layer 2 interface allows the firewall to act as a switch and forward traffic based on MAC addresses.The firewall can send and receive traffic from a layer 2 interface and apply security policies and inspect the traffic based on the source and destination zones of the interface3.
Start a Discussions
Where does a user assign a tag group to a policy rule in the policy creation window?
Correct : B
A user can assign a tag group to a policy rule in the policy creation window by selecting the General tab. A tag group is a collection of tags that can be used to identify and filter policy rules based on different criteria, such as function, location, or priority.A user can create a tag group on Panorama and assign it to a policy rule to apply the same set of tags to multiple firewalls or device groups1. To assign a tag group to a policy rule, the user needs to:
Select the General tab in the policy creation window.
Click the Tag Group drop-down menu and select the tag group that the user wants to assign to the policy rule.
Click OK to save the changes. The policy rule will inherit the tags from the tag group and display them in the Tag column.
Start a Discussions
Which policy set should be used to ensure that a policy is applied just before the default security rules?
Correct : D
The policy set that should be used to ensure that a policy is applied just before the default security rules is the shared post-rulebase. The shared post-rulebase is a set of Security policy rules that are defined on Panorama and apply to all firewalls or device groups. The shared post-rulebase is evaluated after the local firewall policy and the child device-group post-rulebase, but before the default security rules.The shared post-rulebase can be used to enforce common security policies across multiple firewalls or device groups, such as blocking high-risk applications or traffic1.Reference:Security Policy Rule Hierarchy,Security Policy Rulebase,Certifications - Palo Alto Networks,Palo Alto Networks Certified Network Security Administrator (PAN-OS 10.0)or [Palo Alto Networks Certified Network Security Administrator (PAN-OS 10.0)].
Start a Discussions
Review the Screenshot:
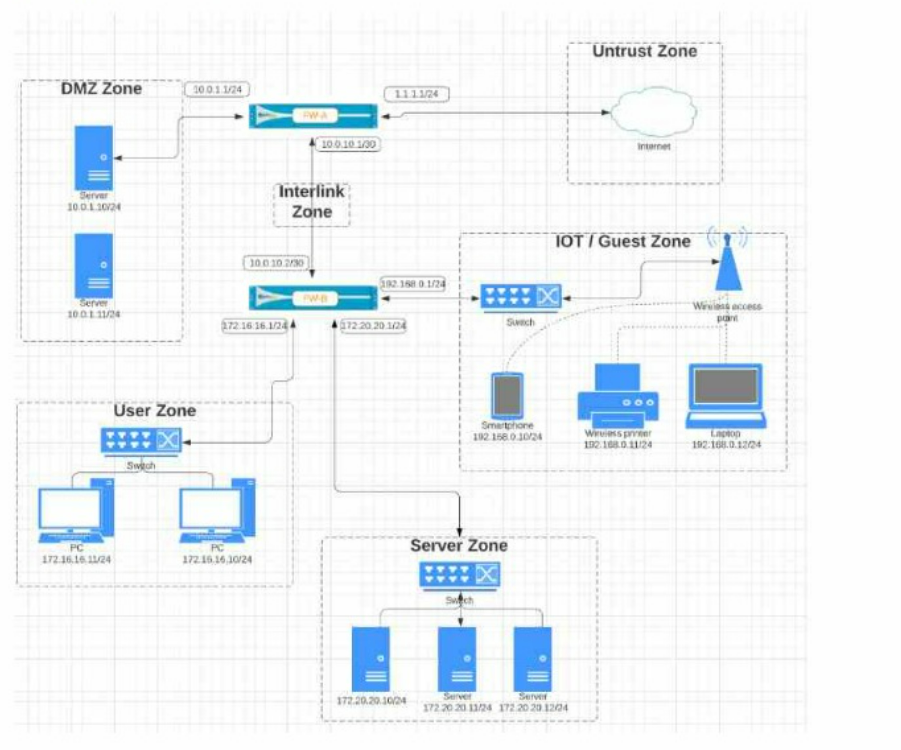
Given the network diagram, traffic must be permitted for SSH and MYSQL from the DMZ to the SERVER zones, crossing two firewalls. In addition, traffic should be permitted from the
SERVER zone to the DMZ on SSH only.
Which rule group enables the required traffic?
A)
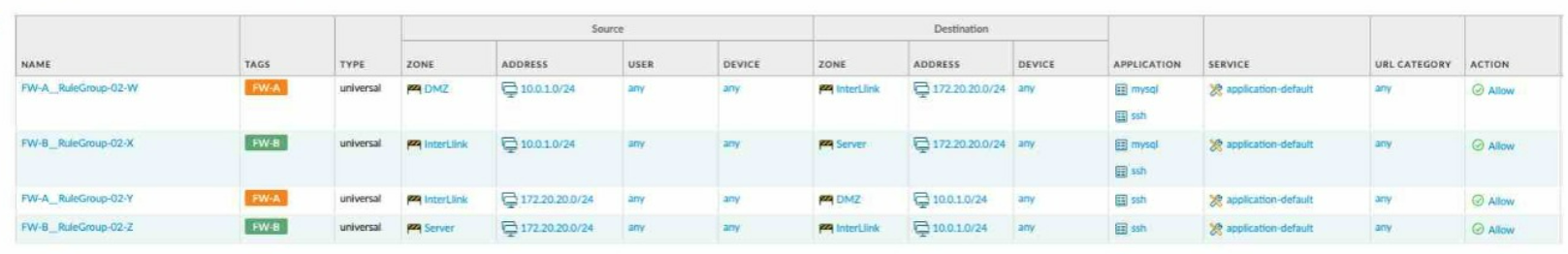
B)
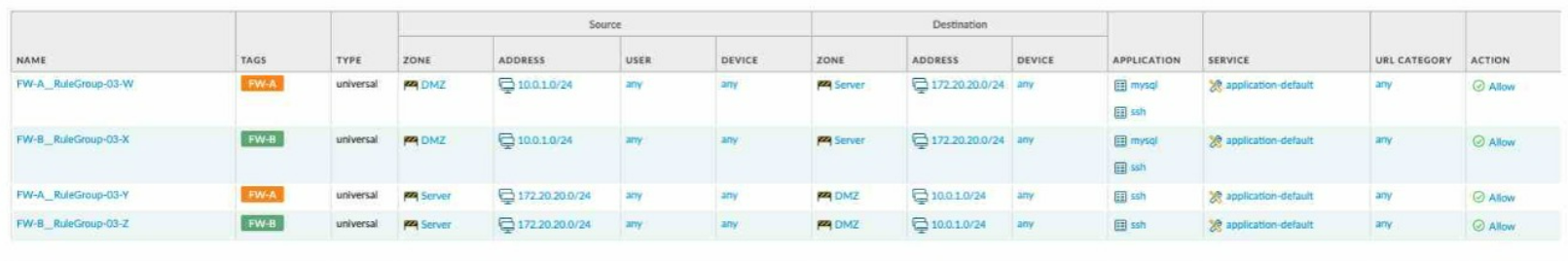
C)
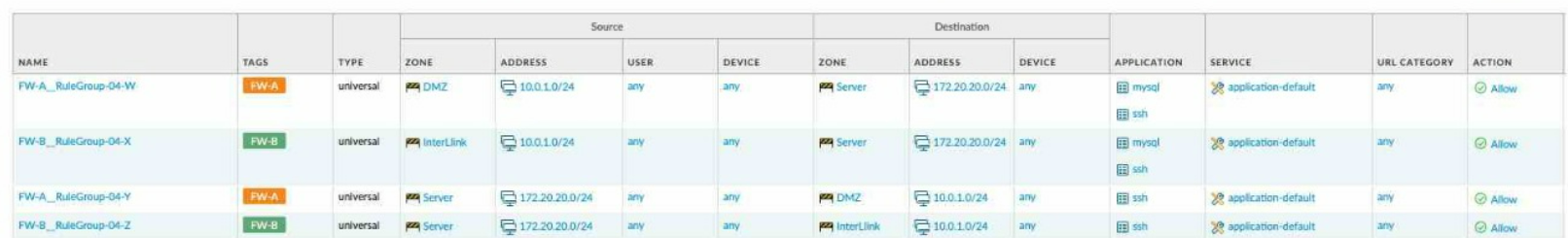
D)
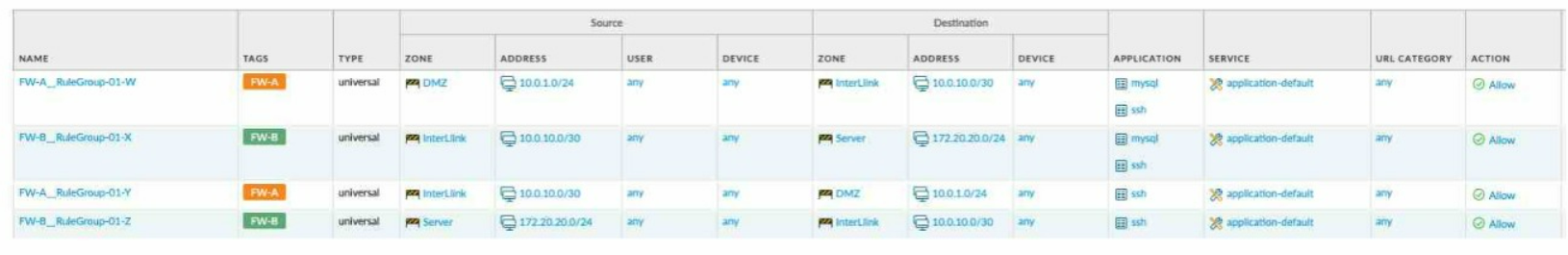
Correct : B
Start a Discussions