Master Netskope NSK200 Exam with Reliable Practice Questions
Review the exhibit.
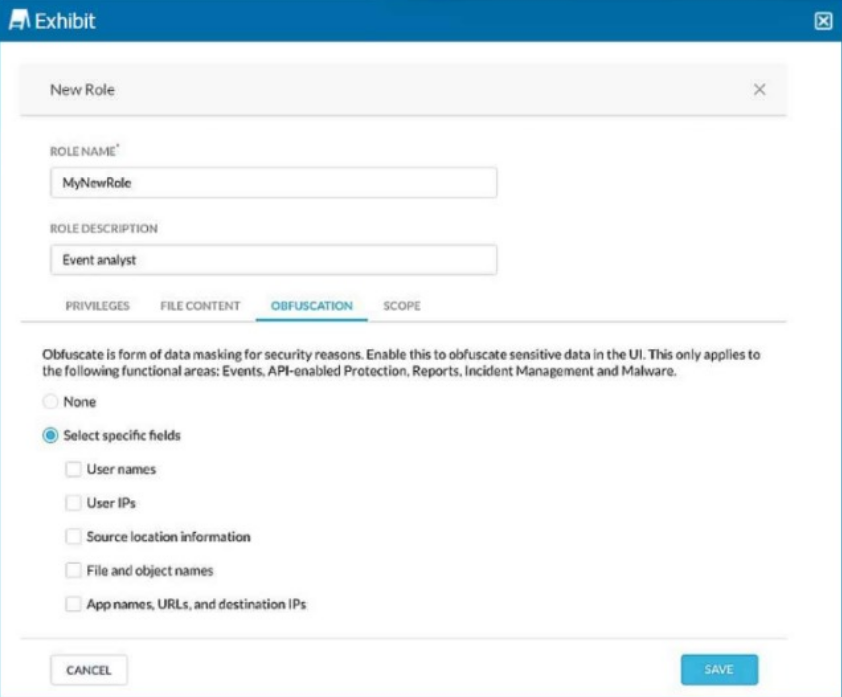
You are asked to create a new role that allows analysts to view Events and Reports while providing user privacy. You need to avoid directly exposing identities and user location information.
Which three fields must you obfuscate in this scenario? (Choose three.)
Correct : A, B, E
To ensure user privacy in the Events and Reports view, obfuscate sensitive information like User IPs, User names, and Source location information. This helps protect identities and prevent location tracking of users while allowing visibility into activity details.
Start a Discussions
Your company is using on-premises QRadar as a SIEM solution. They are replacing it with Rapid7 in the cloud. The legacy on-premises QRadar will eventually be decommissioned. Your IT department does not want to use the same token that QRadar uses.
Correct : C
Netskope REST API v2 supports multiple tokens, allowing different applications or integrations (like QRadar and Rapid7) to have distinct tokens. This avoids token conflicts and enhances security by isolating access permissions for different SIEM systems.
Start a Discussions
You are deploying a Netskope client in your corporate office network. You are aware of firewall or proxy rules that need to be modified to allow traffic.
Which two statements are true in this scenario? (Choose two.)
Correct : C, D
Allowing UDP port 443 is recommended to support DTLS, which enhances performance over the Netskope tunnel. TCP port 443 must also be allowed as it is essential for secure HTTPS connections used by Netskope services.
Start a Discussions
Review the exhibit.
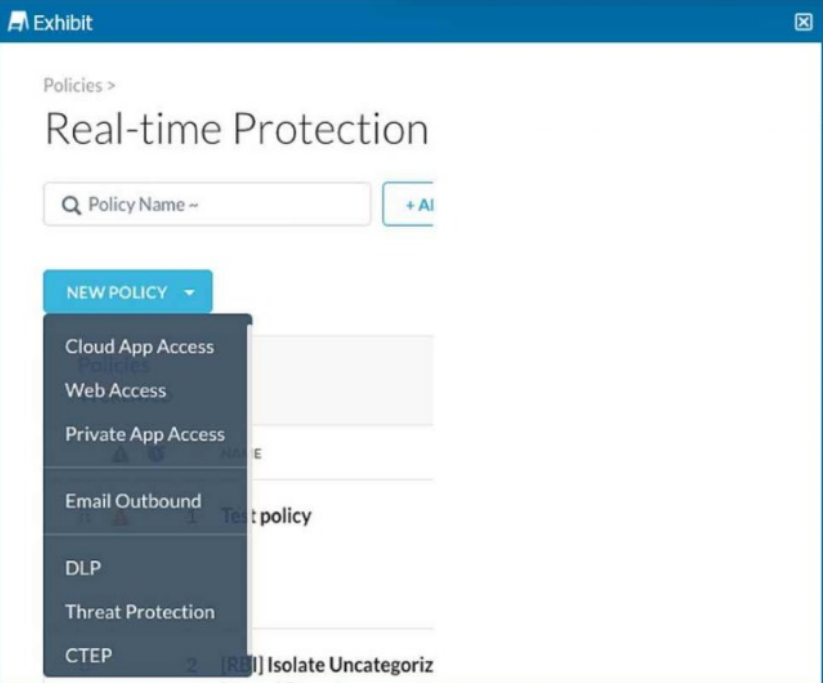
You are asked to create a new Real-time Protection policy to scan SMTP emails using data loss prevention (DLP) for personal health information (PHI). The scope is limited to only emails being sent from Microsoft Exchange Online to outside recipients.
Correct : B
An 'Email Outbound' policy is specifically designed to apply data loss prevention controls on outbound emails, such as SMTP traffic from Exchange Online. This policy type enables granular control over outbound email content, ensuring compliance with DLP policies for PHI data.
Start a Discussions
Your company asks you to use Netskope to integrate with Endpoint Detection and Response (EDR) vendors such as Crowdstrike.
Which two requirements are needed for a successful integration and sharing of threat data? (Choose two.)
Correct : A, C
Integrating with EDR vendors like Crowdstrike requires an API Client ID for authentication and data sharing. A remediation profile is also necessary to define automated actions that can be taken when threats are detected, ensuring effective response to endpoint threats.
Start a Discussions