Master Netskope NSK101 Exam with Reliable Practice Questions
Your customer has cloud storage repositories containing sensitive files of their partners, including bank statements, consulting, and disclosure agreements. In this scenario, which feature would help them control the flow of these types of documents?
Correct : C
Data Loss Prevention (DLP) document classifiers are designed to identify and control the flow of sensitive information based on predefined patterns and criteria. In this scenario, where the customer has cloud storage repositories containing sensitive files such as bank statements, consulting agreements, and disclosure agreements, DLP document classifiers can help:
Identify sensitive documents: By scanning and classifying documents based on their content, DLP document classifiers ensure that sensitive files are recognized and handled appropriately.
Control data flow: Policies can be applied to prevent unauthorized access, sharing, or movement of sensitive files, thereby protecting the data from leakage or exposure.
Netskope DLP documentation, detailing how document classifiers work and how they can be configured to protect sensitive information.
Best practices for implementing DLP solutions to safeguard sensitive data in cloud storage environments.
Start a Discussions
Click the Exhibit button.
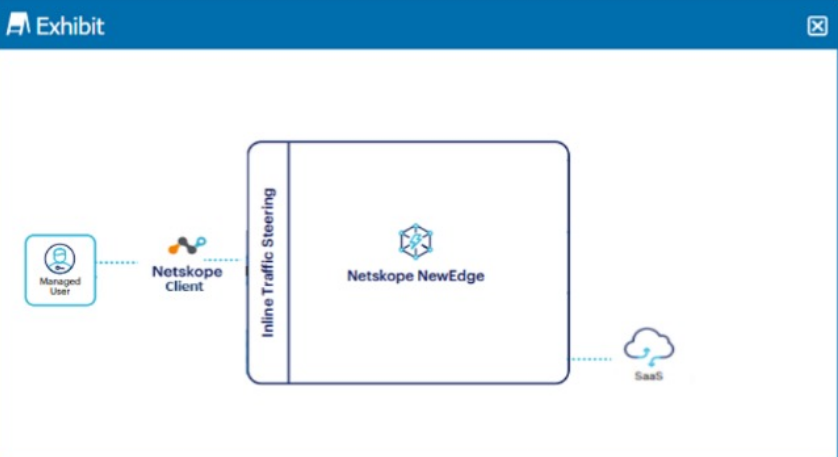
A user is connected to a SaaS application through Netskope's Next Gen SWG with SSL inspection enabled. In this scenario, what information is available in SkopeIT? (Choose three.)
Correct : A, C, D
In the scenario where a user is connected to a SaaS application through Netskope's Next Gen Secure Web Gateway (SWG) with SSL inspection enabled, the following information is available in SkopeIT:
User activity, CCL: SkopeIT provides detailed logs of user activities, including actions taken within SaaS applications, and uses the Cloud Confidence Level (CCL) to rate the trustworthiness of cloud applications.
Account instance, category: It logs information about the specific instance of the account being accessed and categorizes the type of service or application in use, which helps in identifying the context of the user's activities.
Username, source location: The username of the user accessing the SaaS application and their source location (such as IP address or geographic location) are logged for audit and compliance purposes.
Netskope documentation on SSL inspection and SkopeIT logging.
Detailed configuration guides on using Next Gen SWG and the types of data collected by SkopeIT.
Start a Discussions
You are asked to review files affected by malware in your organization. In this scenario, which two actions are possible and would be accessible from the Netskope UI -> Incidents --> Malware? (Choose two)
Correct : B, D
When reviewing files affected by malware in the Netskope UI under Incidents -> Malware, you have the following options:
Identify the exposure of the file identified as malware: This allows you to see where the malware has spread within the organization, which users or systems are affected, and any potential data exposure resulting from the malware.
Determine the Detection Engine used to identify the malware: Netskope provides details on which detection engine (such as AV, sandboxing, or other heuristic engines) identified the malware. This helps in understanding the threat vector and the reliability of the detection.
Downloading the original malware file (option A) is generally not recommended for security reasons and may not be supported directly from the Netskope UI. Remediation of compromised devices (option C) would typically be handled through endpoint security solutions rather than directly from the Netskope UI.
Netskope documentation on malware detection and incident response.
Best practices for handling malware incidents and using the Netskope UI for threat analysis.
Start a Discussions
Your customer asks you to secure all Web traffic as part of the initial configuration. In the Netskope platform, which statement is correct in this scenario?
Correct : A
To secure all web traffic as part of the initial configuration in the Netskope platform, you need to:
Add the all Web traffic option to the steering configuration: This ensures that all web traffic is routed through Netskope for inspection and policy enforcement. By steering all web traffic, you enable Netskope to apply security measures, such as SSL decryption, threat protection, and DLP, to all HTTP and HTTPS traffic.
Netskope does not automatically steer all web traffic by default; it requires configuration in the steering policies. Selecting all web traffic in the SSL decryption section only pertains to decrypting traffic, not the actual steering of the traffic.
Netskope documentation on configuring steering settings and policies.
Guidelines for setting up web traffic steering and SSL decryption in the Netskope platform.
Start a Discussions
As an administrator, you are investigating an increase in the number of incidents related to compromised credentials. You are using the Netskope Compromised Credentials feature on your tenant to assess the situation. Which insights would you find when using this feature? (Choose two)
Correct : A, B
When using the Netskope Compromised Credentials feature, administrators can gain valuable insights into security incidents related to compromised credentials. The insights provided by this feature include:
Compromised usernames: This information helps identify which user accounts have been compromised, allowing administrators to take necessary actions such as resetting passwords and notifying affected users.
Breach information source: Netskope provides details on the source of the breach, such as which third-party service or data breach resulted in the compromise of credentials. This helps in understanding the context of the breach and implementing measures to prevent future incidents.
While compromised passwords (option C) are indirectly involved, they are not explicitly listed as an insight provided by this feature. Similarly, affected managed applications (option D) are related but not directly part of the primary insights.
Netskope documentation on Compromised Credentials feature and incident response.
Security best practices for managing and mitigating compromised credential incidents.
Start a Discussions