Master Juniper JN0-649 Exam with Reliable Practice Questions
You recently committed a change to a router to reject OSPF routes sourced from area 10. However, you are still seeing area 10 routes in the routing table.
Referring to the exhibit, which statement is correct?
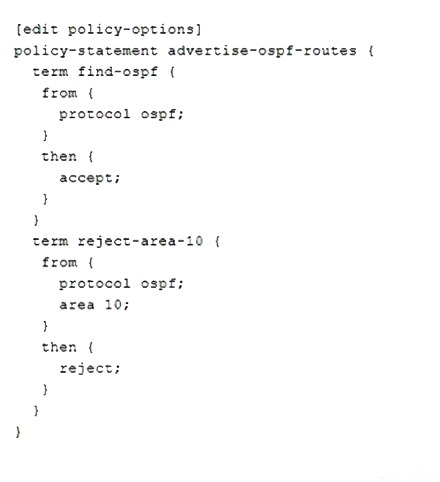
Correct : A
Once a route is accepted, no other terms in the routing policy are evaluated.
Start a Discussions
In OSPF, how does a router ensure that LSAs advertised to a neighboring router are received?
Correct : C
Start a Discussions
There are two BGP routes to 10.200.200.0/24 received from two external peers. Route 1 comes from a neighbor with a router ID of 10.10.100.1 and a peer IP address of 10.10.30.1, and route 2 comes from a neighbor with a router ID of 10.10.200.1 and a peer IP address of 10.10.50.1. Both routes have the same MED value, origin value, AS path length, and local preference number.
In this scenario, which statement is correct about the active route?
Correct : C
The router determines the router ID for each peer that advertised a path to the route destination. A lower router ID value is preferred over a higher router ID value. 10. The router determines the peer ID for each peer that advertised a path to the router destination. A lower peer ID value is preferred over a higher peer ID value. The peer ID is the IP address of the established BGP peering session.
Start a Discussions
You are asked to configure 802.1X on your access ports to allow only a single device to authenticate.
In this scenario, which configuration would you use?
Correct : C
Single supplicant mode authenticates only the first end device that connects to an authenticator port. All other end devices connecting to the authenticator port after the first has connected successfully, whether they are 802.1X-enabled or not, are permitted access to the port without further authentication. If the first authenticated end device logs out, all other end devices are locked out until an end device authenticates. Single-secure supplicant mode authenticates only one end device to connect to an authenticator port. No other end device can connect to the authenticator port until the first logs out.
Start a Discussions
Referring to the exhibit, how will router E quickly learn that the remote MAC addresses are no longer reachable through the router attached to the failed link?
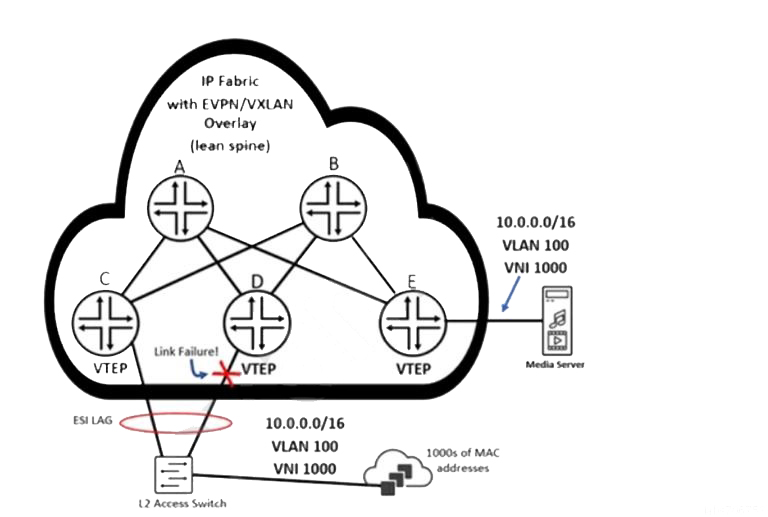
Correct : B
Start a Discussions