Master Juniper JN0-214 Exam with Reliable Practice Questions
Click the Exhibit button.
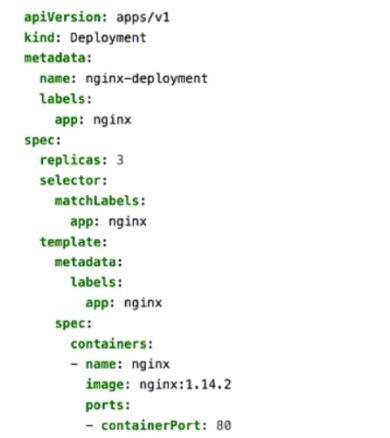
You apply the manifest file shown in the exhibit.
Which two statements are correct in this scenario? (Choose two.)
Correct : A, B
The provided YAML manifest defines a Kubernetes Deployment object that creates and manages a set of pods running the NGINX web server. Let's analyze each statement in detail:
A . The created pods are receiving traffic on port 80.
Correct:
The containerPort: 80 field in the manifest specifies that the NGINX container listens on port 80 for incoming traffic.
While this does not expose the pods externally, it ensures that the application inside the pod (NGINX) is configured to receive traffic on port 80.
B . This manifest is used to create a deployment.
Correct:
The kind: Deployment field explicitly indicates that this manifest is used to create a Kubernetes Deployment .
Deployments are used to manage the desired state of pods, including scaling, rolling updates, and self-healing.
C . This manifest is used to create a deploymentConfig.
Incorrect:
deploymentConfig is a concept specific to OpenShift, not standard Kubernetes. In OpenShift, deploymentConfig provides additional features like triggers and lifecycle hooks, but this manifest uses the standard Kubernetes Deployment object.
D . Four pods are created as a result of applying this manifest.
Incorrect:
The replicas: 3 field in the manifest specifies that the Deployment will create three replicas of the NGINX pod. Therefore, only three pods are created, not four.
Why These Statements?
Traffic on Port 80:
The containerPort: 80 field ensures that the NGINX application inside the pod listens on port 80. This is critical for the application to function as a web server.
Deployment Object:
The kind: Deployment field confirms that this manifest creates a Kubernetes Deployment, which manages the lifecycle of the pods.
Replica Count:
The replicas: 3 field explicitly states that three pods will be created. Any assumption of four pods is incorrect.
Additional Context:
Kubernetes Deployments: Deployments are one of the most common Kubernetes objects used to manage stateless applications. They ensure that the desired number of pod replicas is always running and can handle updates or rollbacks seamlessly.
Ports in Kubernetes: The containerPort field in the pod specification defines the port on which the containerized application listens. However, to expose the pods externally, a Kubernetes Service (e.g., NodePort, LoadBalancer) must be created.
JNCIA Cloud Reference:
The JNCIA-Cloud certification covers Kubernetes concepts, including Deployments, Pods, and networking. Understanding how Deployments work and how ports are configured is essential for managing containerized applications in cloud environments.
For example, Juniper Contrail integrates with Kubernetes to provide advanced networking and security features for Deployments like the one described in the exhibit.
Kubernetes Documentation: Deployments
Kubernetes Documentation: Pod Networking
Juniper JNCIA-Cloud Study Guide: Kubernetes Architecture
Start a Discussions
You are asked to support an application in your cluster that uses a non-IP protocol.
In this scenario, which type of virtual network should you create to support this application?
Correct : B
In cloud environments, virtual networks are used to support applications that may rely on different protocols for communication. Let's analyze each option:
A . a Layer 3 virtual network
Incorrect: A Layer 3 virtual network operates at the IP level and is designed for routing traffic between subnets or networks. It is not suitable for applications that use non-IP protocols (e.g., Ethernet-based protocols).
B . a Layer 2 virtual network
Correct: A Layer 2 virtual network operates at the data link layer (Layer 2) and supports non-IP protocols by forwarding traffic based on MAC addresses. This makes it ideal for applications that rely on protocols like Ethernet, MPLS, or other Layer 2 technologies.
C . an Ethernet VPN (EVPN) Type 5 virtual network
Incorrect: EVPN Type 5 is a Layer 3 overlay technology used for inter-subnet routing in EVPN environments. It is not designed to support non-IP protocols.
D . a virtual network router connected to the virtual network
Incorrect: A virtual network router is used to route traffic between different subnets or networks. It operates at Layer 3 and is not suitable for applications using non-IP protocols.
Why Layer 2 Virtual Network?
Support for Non-IP Protocols: Layer 2 virtual networks forward traffic based on MAC addresses, making them compatible with non-IP protocols.
Flexibility: They can support a wide range of applications, including those that rely on Ethernet or other Layer 2 technologies.
JNCIA Cloud Reference:
The JNCIA-Cloud certification covers virtual networking concepts, including Layer 2 and Layer 3 networks. Understanding the differences between these layers is essential for designing networks that meet application requirements.
For example, Juniper Contrail supports Layer 2 virtual networks to enable seamless communication for applications using non-IP protocols.
Virtual Networking Documentation
Juniper JNCIA-Cloud Study Guide: Virtual Networks
Start a Discussions
Which virtualization method requires less duplication of hardware resources?
Correct : A
Virtualization methods differ in how they utilize hardware resources. Let's analyze each option:
A . OS-level virtualization
Correct: OS-level virtualization (e.g., containers) uses the host operating system's kernel to run isolated user-space instances (containers). Since containers share the host OS kernel, there is less duplication of hardware resources compared to other virtualization methods.
B . hardware-assisted virtualization
Incorrect: Hardware-assisted virtualization (e.g., Intel VT-x, AMD-V) enables full virtual machines (VMs) to run on physical hardware. Each VM includes its own operating system, leading to duplication of resources like memory and CPU.
C . full virtualization
Incorrect: Full virtualization involves running a complete guest operating system on top of a hypervisor. Each VM requires its own OS, resulting in significant resource duplication.
D . paravirtualization
Incorrect: Paravirtualization modifies the guest operating system to communicate directly with the hypervisor. While it reduces some overhead compared to full virtualization, it still requires separate operating systems for each VM, leading to resource duplication.
Why OS-Level Virtualization?
Resource Efficiency: Containers share the host OS kernel, eliminating the need for multiple operating systems and reducing resource duplication.
Lightweight: Containers are faster to start and consume fewer resources compared to VMs.
JNCIA Cloud Reference:
The JNCIA-Cloud certification emphasizes understanding virtualization technologies, including OS-level virtualization. Containers are a key component of modern cloud-native architectures due to their efficiency and scalability.
For example, Juniper Contrail integrates with container orchestration platforms like Kubernetes to manage OS-level virtualization workloads efficiently.
Docker Documentation: Container Basics
Juniper JNCIA-Cloud Study Guide: Virtualization
Start a Discussions
Which encapsulation protocol uses tunneling to provide a Layer 2 overlay over an underlying Layer 3 network?
Correct : C
Encapsulation protocols are used to create overlay networks that provide connectivity over an underlying network. Let's analyze each option:
A . VLAN
Incorrect: VLANs operate at Layer 2 and are limited to a single physical network. They do not provide tunneling or overlay capabilities over a Layer 3 network.
B . IPsec
Incorrect: IPsec is a security protocol used to encrypt and authenticate IP packets. It does not provide Layer 2 overlay capabilities.
C . VXLAN
Correct: VXLAN (Virtual Extensible LAN) is an encapsulation protocol that creates a Layer 2 overlay network over an underlying Layer 3 network. It encapsulates Layer 2 Ethernet frames within UDP packets, enabling scalable and flexible network architectures.
D . GRE
Incorrect: GRE (Generic Routing Encapsulation) is a tunneling protocol that encapsulates packets but does not inherently provide Layer 2 overlay capabilities. It is typically used for point-to-point tunnels.
Why VXLAN?
Layer 2 Overlay: VXLAN extends Layer 2 networks across Layer 3 boundaries, enabling seamless communication between distributed environments.
Scalability: VXLAN supports up to 16 million virtual networks, making it ideal for large-scale cloud deployments.
JNCIA Cloud Reference:
The JNCIA-Cloud certification covers overlay networking protocols like VXLAN as part of its curriculum on cloud architectures. Understanding VXLAN is essential for designing scalable and resilient virtual networks.
For example, Juniper Contrail uses VXLAN to extend virtual networks across data centers, ensuring consistent connectivity and isolation.
VXLAN RFC 7348
Juniper JNCIA-Cloud Study Guide: Overlay Networking
Start a Discussions
A. kubelet
Correct : C
This question seems to be asking about a Kubernetes component that is responsible for running containers. Let's analyze each option:
A . kubelet
Incorrect: The kubelet is responsible for managing the state of pods and containers on a worker node. It ensures that containers are running as expected but does not directly execute or run the containers.
B . kube-proxy
Incorrect: The kube-proxy manages network communication for services and pods by implementing load balancing and routing rules. It does not handle the execution of containers.
C . container runtime
Correct: The container runtime (e.g., containerd, cri-o) is the component that actually runs and manages containers on a Kubernetes node. It interacts with the operating system to start, stop, and manage containerized applications.
D . kube controller
Incorrect: The kube controller is part of the control plane and ensures that the desired state of the cluster (e.g., number of replicas) is maintained. It does not directly run containers.
Why Container Runtime?
Execution of Containers: The container runtime is responsible for pulling container images, starting containers, and managing their lifecycle.
Integration with Kubernetes: Kubernetes communicates with the container runtime through the Container Runtime Interface (CRI).
JNCIA Cloud Reference:
The JNCIA-Cloud certification covers Kubernetes architecture, including the role of the container runtime. Understanding how containers are executed is essential for managing Kubernetes clusters.
For example, Juniper Contrail integrates with Kubernetes to provide networking and security for containerized workloads, relying on the container runtime to execute applications.
Kubernetes Documentation: Container Runtimes
Juniper JNCIA-Cloud Study Guide: Kubernetes Architecture
Start a Discussions