Master HPE6-A84 Exam with Reliable Practice Questions
You are working with a developer to design a custom NAE script for a customer. The NAE agent should trigger an alert when ARP inspection drops packets on a VLAN. The customer wants the admins to be able to select the correct VLAN ID for the agent to monitor when they create the agent.
What should you tell the developer to do?
Correct : B
A custom NAE script is a Python script that defines the monitors, the alert-trigger logic, and the remedial actions for an NAE agent. A monitor is a URI that specifies the data source and the data type that the NAE agent should collect and analyze. For example, to monitor the ARP inspection statistics on a VLAN, the monitor URI would be something like this:
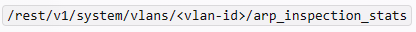
where <vlan-id> is the ID of the VLAN to be monitored.
To allow the admins to select the correct VLAN ID for the agent to monitor when they create the agent, you need to define a VLAN ID parameter in the NAE script. A parameter is a variable that can be set by the user when creating or modifying an agent. A parameter can be referenced in other parts of the script by using the syntax ${parameter-name}. For example, to define a VLAN ID parameter and reference it in the monitor URI, you would write something like this:
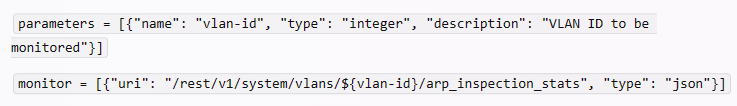
This way, when the admins create or modify the agent, they can enter the VLAN ID that they want to monitor, and the NAE script will use that value in the monitor URI.
Start a Discussions
You want to use Device Insight tags as conditions within CPPM role mapping or enforcement policy rules.
What guidelines should you follow?
Correct : D
Option A is incorrect because creating an HTTP authentication source to the Central API is not necessary to use Device Insight tags as conditions. Device Insight tags are already synchronized between Central and CPPM, and can be accessed from the Endpoint Repository.
Option B is incorrect because using the Application type for the rule conditions is not applicable to Device Insight tags. The Application type is used to match attributes from the Application Authentication source, which is used to integrate with third-party applications such as Microsoft Intune or Google G Suite.
Option C is incorrect because using the Endpoints Repository type for the rule conditions is not valid for Device Insight tags. The Endpoints Repository type is used to match attributes from the Endpoints Repository source, which is different from the Endpoint type. The Endpoints Repository source contains information about endpoints that are manually added or imported into CPPM, while the Endpoint type contains information about endpoints that are dynamically discovered and profiled by CPPM or Device Insight. Adding Endpoints Repository as a secondary authentication source for services that use policies with these rules is also unnecessary and redundant.
Start a Discussions
Refer to the scenario.
A customer has asked you to review their AOS-CX switches for potential vulnerabilities. The configuration for these switches is shown below:
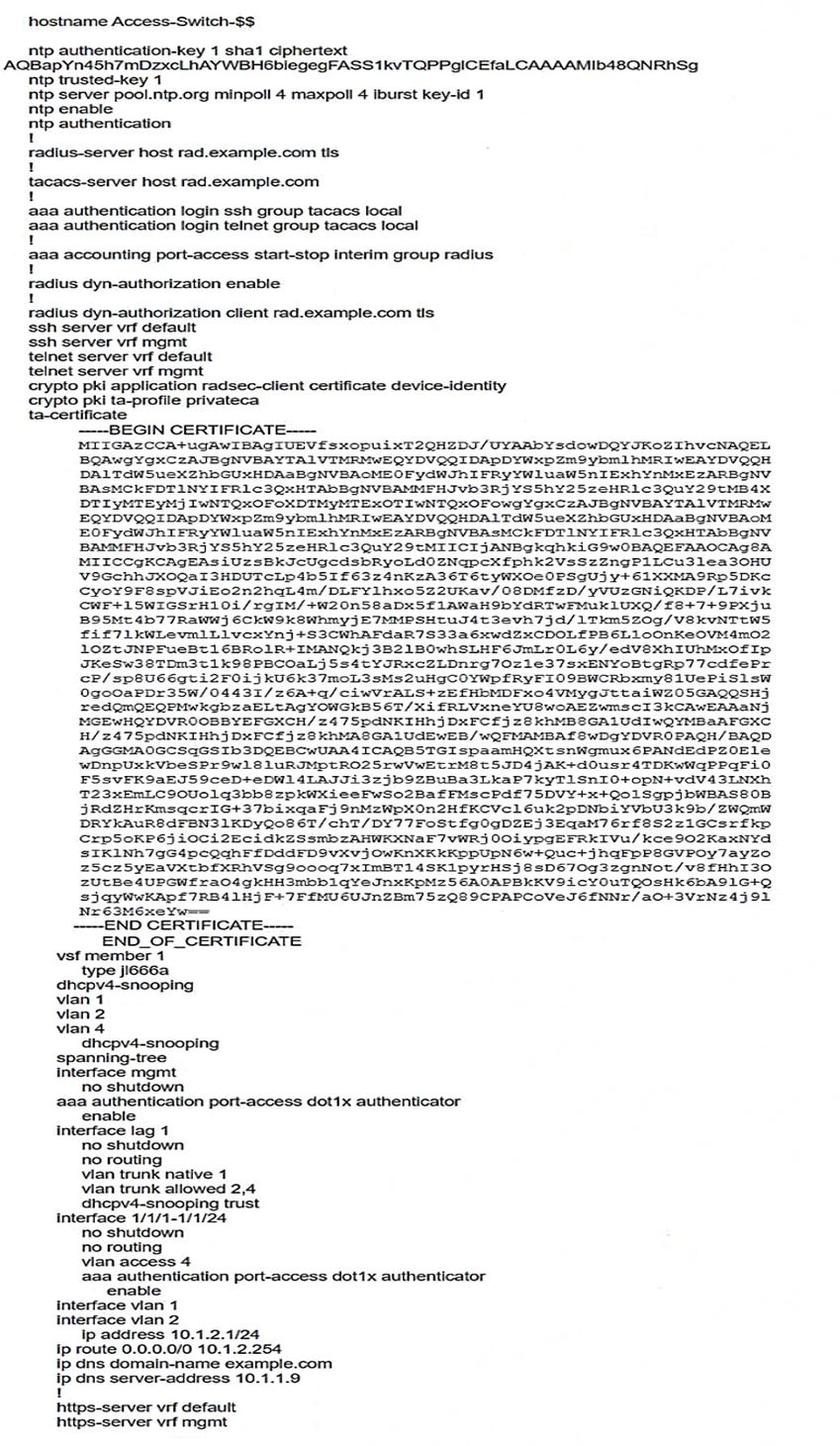
What is one recommendation to make?
Start a Discussions
Refer to the scenario.
A customer has asked you to review their AOS-CX switches for potential vulnerabilities. The configuration for these switches is shown below:
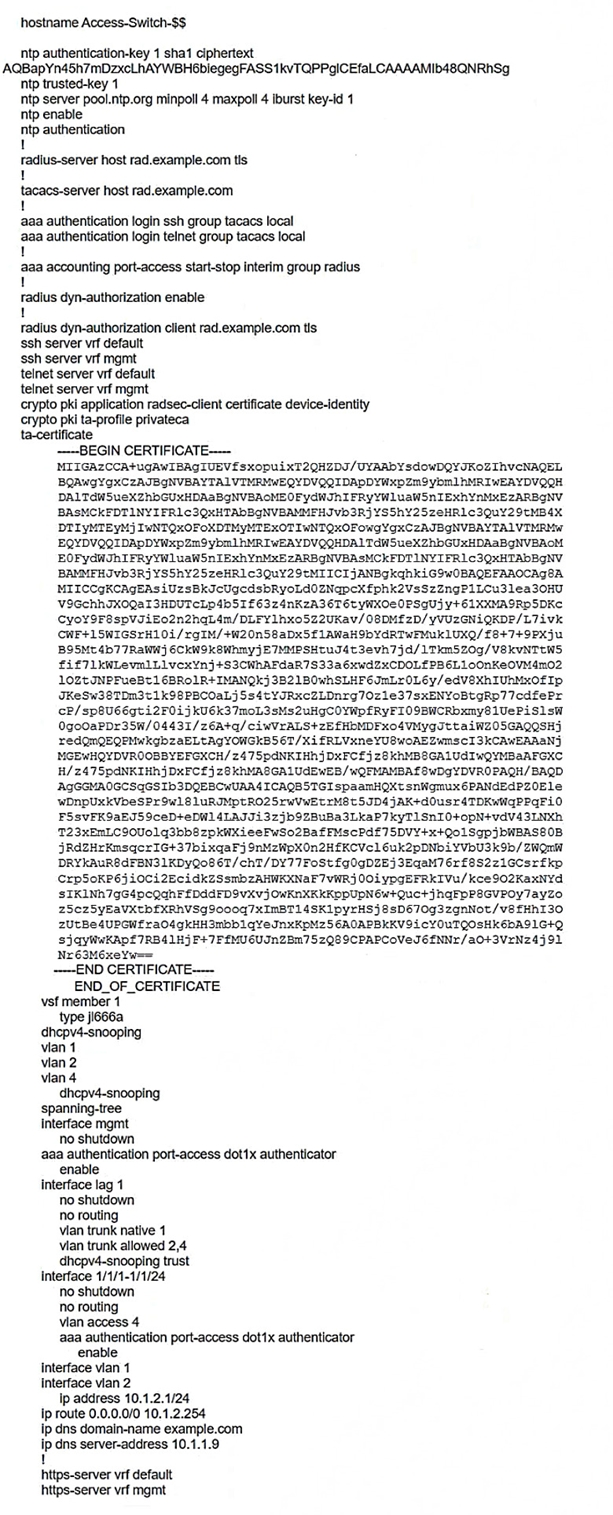
What is one immediate remediation that you should recommend?
Start a Discussions
Refer to the exhibit.
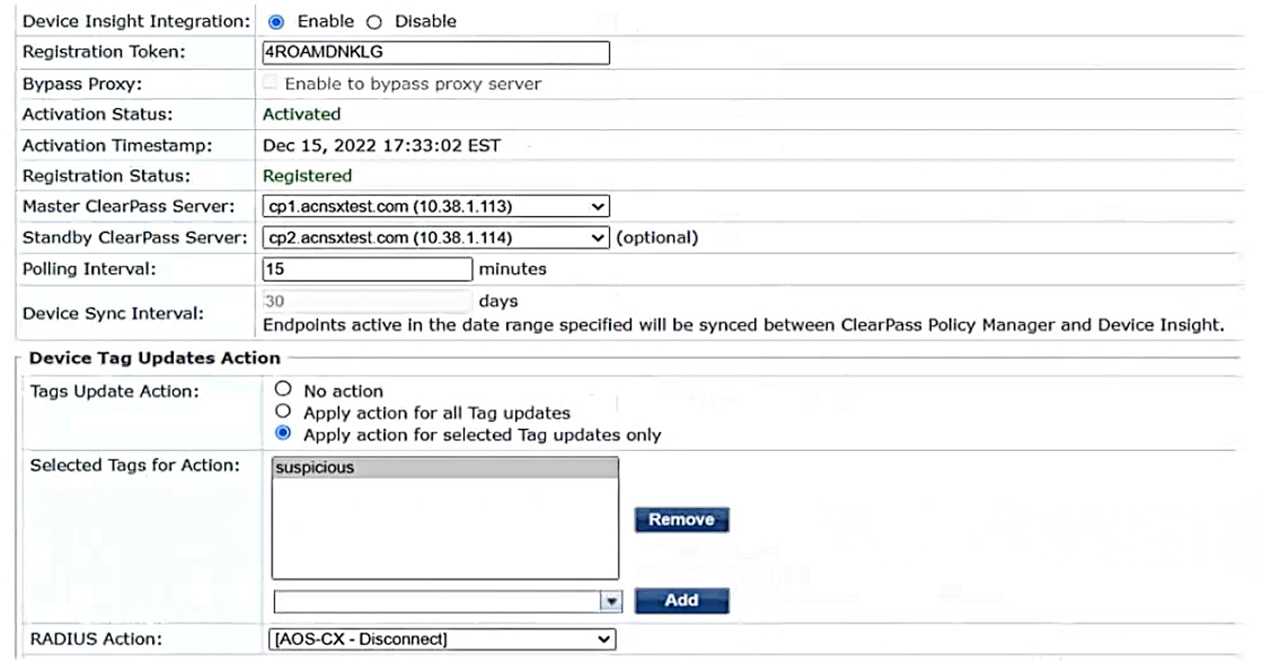
Aruba ClearPass Policy Manager (CPPM) is using the settings shown in the exhibit. You reference the tag shown in the exhibit in enforcement policies related to NASes of several types, including Aruba APs, Aruba gateways, and AOS-CX switches.
What should you do to ensure that clients are reclassified and receive the correct treatment based on the tag?
Start a Discussions