Master Fortinet NSE8_812 Exam with Reliable Practice Questions
Start a Discussions
A customer wants to use the FortiAuthenticator REST API to retrieve an SSO group called SalesGroup. The following API call is being made with the 'curl' utility:

Which two statements correctly describe the expected behavior of the FortiAuthenticator REST API? (Choose two.)
Correct : B, D
To retrieve an SSO group called SalesGroup using the FortiAuthenticator REST API, the following issues need to be fixed in the API call:
The API version should be v2, not v1, as SSO groups are only supported in version 2 of the REST API.
The HTTP method should be GET, not POST, as GET is used to retrieve information from the server, while POST is used to create or update information on the server. Therefore, a correct API call would look like this: curl -X GET -H ''Authorization: Bearer <token>'' https://fac.example.com/api/v2/sso/groups/SalesGroup References: https://docs.fortinet.com/document/fortiauthenticator/6.4.1/rest-api-solution-guide/927310/introduction https://docs.fortinet.com/document/fortiauthenticator/6.4.1/rest-api-solution-guide/927311/sso-groups
Start a Discussions
Refer to the exhibit.
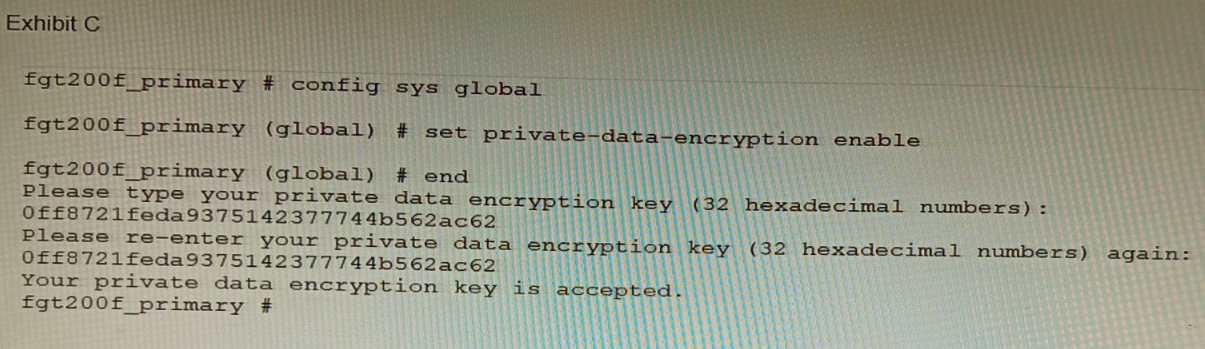
A customer has deployed a FortiGate 200F high-availability (HA) cluster that contains & TPM chip. The exhibit shows output from the FortiGate CLI session where the administrator enabled TPM.
Following these actions, the administrator immediately notices that both FortiGate high availability (HA) status and FortiManager status for the FortiGate are negatively impacted.
What are the two reasons for this behavior? (Choose two.)
Correct : A, B
The two reasons for the negative impact on the FortiGate HA status and FortiManager status after enabling TPM are:
The private-data-encryption key entered on the primary unit did not match the value that the TPM expected. This could happen if the TPM was previously enabled and then disabled, and the key was changed in between. The TPM will reject the new key and cause an error in the configuration synchronization.
Configuration for TPM is not synchronized between FortiGate HA cluster members. Each cluster member must have the same private-data-encryption key to form a valid HA cluster and synchronize their configurations. However, enabling TPM on one unit does not automatically enable it on the other units, and the key must be manually entered on each unit. To resolve these issues, the administrator should disable TPM on all units, clear the TPM data, and then enable TPM again with the same private-data-encryption key on each unit. References: https://docs.fortinet.com/document/fortigate/6.4.0/cookbook/103437/inbound-ssl-inspection https://docs.fortinet.com/document/fortigate/6.4.0/cookbook/103438/application-detection-on-ssl-offloaded-traffic
Start a Discussions
Refer to the exhibits.

The exhibits show a FortiMail network topology, Inbound configuration settings, and a Dictionary Profile.
You are required to integrate a third-party's host service (srv.thirdparty.com) into the e-mail processing path.
All inbound e-mails must be processed by FortiMail antispam and antivirus with FortiSandbox integration. If the email is clean, FortiMail must forward it to the third-party service, which will send the email back to FortiMail for final delivery, FortiMail must not scan the e-mail again.
Which three configuration tasks must be performed to meet these requirements? (Choose three.)
Correct : A, B, E
Ais correct because the scan order must be changed to antispam-sandbox-content in order for FortiMail to scan the email for spam and viruses before forwarding it to the third-party service.
Bis correct because the Catch-All profile must be applied to the CFInbound profile in order for FortiMail to forward clean emails to the third-party service.
Eis correct because an IP policy must be created with a Source value of 100.64.0.72/32 in order to allow emails from the third-party service to be delivered to FortiMail.
The other options are not necessary to meet the requirements. Option C is not necessary because the access receive rule will already allow emails from the third-party service to be received by FortiMail. Option D is not necessary because the Catch-All profile already allows emails to be delivered to any destination.
Here are some additional details about integrating a third-party service into the FortiMail email processing path:
The third-party service must be able to receive emails from FortiMail and send them back to FortiMail.
The third-party service must be able to communicate with FortiMail using the SMTP protocol.
The third-party service must be able to authenticate with FortiMail using the SMTP AUTH protocol.
Once the third-party service is integrated into the FortiMail email processing path, all inbound emails will be processed by FortiMail as usual. If the email is clean, FortiMail will forward it to the third-party service. The third-party service will then send the email back to FortiMail for final delivery. FortiMail will not scan the email again.
Start a Discussions
Review the following FortiGate-6000 configuration excerpt:
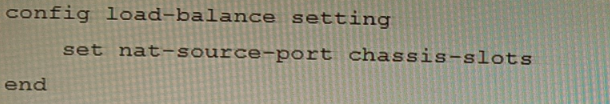
Based on the configuration, which statement is correct regarding SNAT source port partitioning behavior?
Correct : A
The configuration excerpt shows that the SNAT source port partitioning behavior is set to dynamic. This means that the FortiGate will dynamically distribute SNAT source ports to operating FPCs or FPMs. This ensures that active sessions are not interrupted if an FPC or FPM goes down.
The other options are incorrect. Option B is incorrect because the default SNAT configuration is static. Option C is incorrect because the configuration excerpt does not specify that SNAT source ports are statically distributed. Option D is incorrect because the SNAT source ports are not evenly distributed across chassis slots.
Here are some additional details about SNAT source port partitioning behavior:
SNAT source port partitioning behavior can be set todynamicorstatic.
The default SNAT configuration isstatic.
Dynamic SNAT source port partitioning ensures that active sessions are not interrupted if an FPC or FPM goes down.
Static SNAT source port partitioning can improve performance by reducing the number of SNAT lookups.
Start a Discussions