Master Fortinet NSE7_PBC-7.2 Exam with Reliable Practice Questions
You are troubleshooting an Azure SDN connectivity issue with your FortiGate VM
Which two queries does that SDN connector use to interact with the Azure management API? (Choose two.)
Start a Discussions
When adding the Amazon Web Services (AWS) account to the FortiCNP, which three mandatory configuration steps must you follow? (Choose three.)
Correct : A, C, E
When adding the Amazon Web Services (AWS) account to the FortiCNP, you must follow these three mandatory configuration steps:
https://docs.fortinet.com/document/forticnp/22.4.a/online-help/246021/add-aws-account-automatically
Start a Discussions
Refer to the exhibit
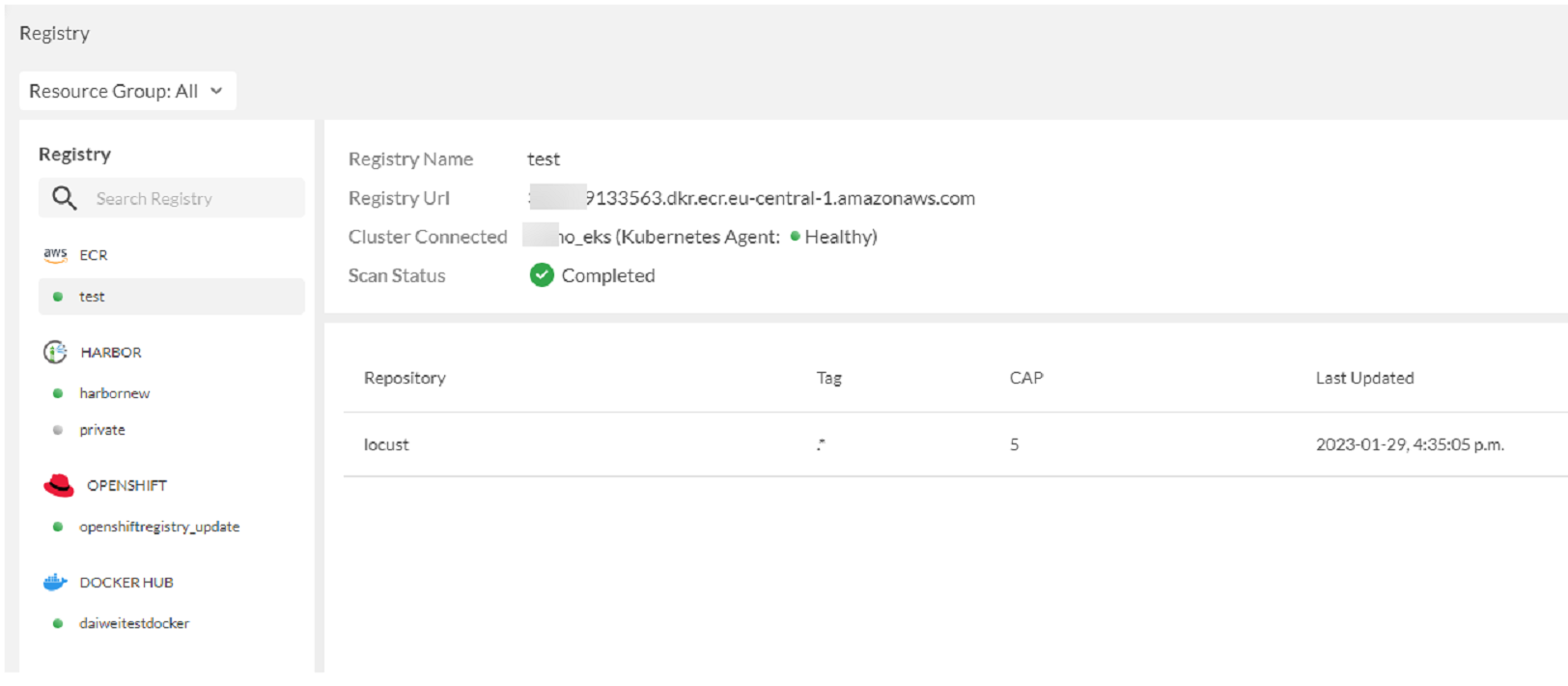
The exhibit shows the results of a FortiCNP registry scan
Which two statements are correct? (Choose two )
Start a Discussions
A customer would like to use FortiGate fabric integration With FortiCNP
When configuring a FortiGate VM to add to FortiCNP, which three mandatory configuration steps must you follow on FortiGate? (Choose three.)
Correct : A, B, D
To configure a FortiGate VM to add to FortiCNP, you need to perform three steps on FortiGate:
Enable send logs in FortiGate to allow FortiCNP to receive the IPS logs from FortiGate.
Create an SSL/SSH inspection profile on FortiGate to inspect the encrypted traffic and apply IPS protection.
Create an IPS sensor and a firewall policy on FortiGate to enable IPS detection and prevention for the traffic.
Start a Discussions
How does an administrator secure container environments from newly emerged security threats?
Correct : D
Securing container environments from newly emerged security threats involves employing specific security mechanisms tailored to the technology and structure of containers. In this context, the use of Docker-related application control signatures (Option D) is critical for effectively managing and mitigating threats in containerized environments.
Docker-Specific Threats: Docker containers, being a prevalent form of container technology, are targeted by various security threats, including those that exploit vulnerabilities specific to the Docker environment and runtime. Using Docker-related application control signatures means implementing security measures that are specifically designed to detect and respond to anomalies and threats that are unique to Docker containers.
Application Control Signatures: These are sets of definitions that help identify and block potentially malicious activities within application traffic. By focusing on Docker-related signatures, administrators can ensure that the security tools are finely tuned to the operational specifics of Docker containers, thereby providing a robust defense against exploits that target container-specific vulnerabilities.
Start a Discussions