Master Eccouncil 312-39 Exam with Reliable Practice Questions
What type of event is recorded when an application driver loads successfully in Windows?
Correct : D
Start a Discussions
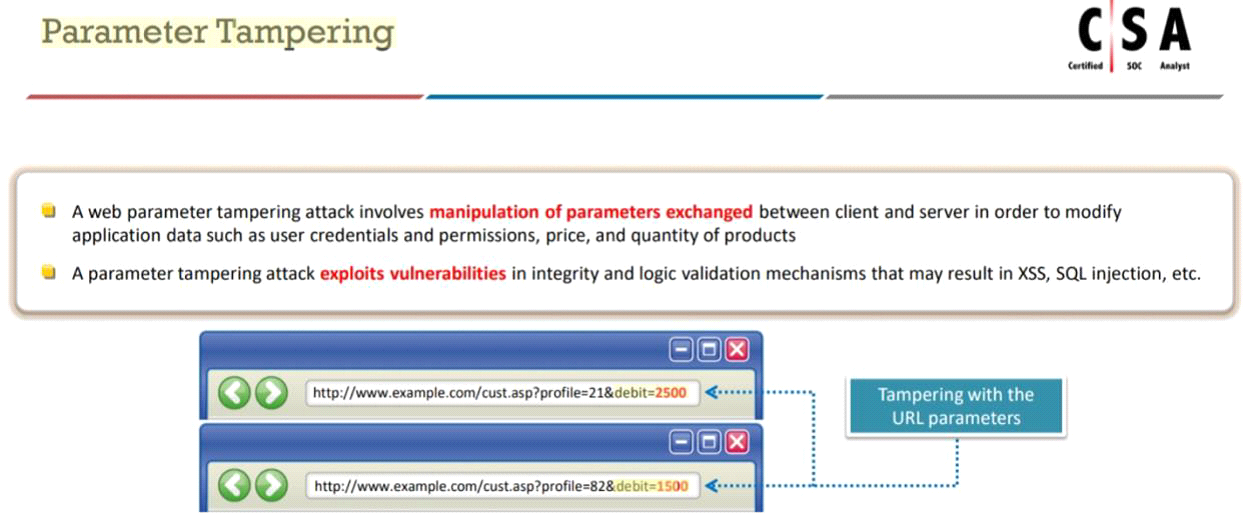
An attacker exploits the logic validation mechanisms of an e-commerce website. He successfully purchases a product worth $100 for $10 by modifying the URL exchanged between the client and the server.
Identify the attack depicted in the above scenario.
Correct : C
Start a Discussions
John, a threat analyst at GreenTech Solutions, wants to gather information about specific threats against the organization. He started collecting information from various sources, such as humans, social media, chat room, and so on, and created a report that contains malicious activity.
Which of the following types of threat intelligence did he use?
Correct : D
Start a Discussions
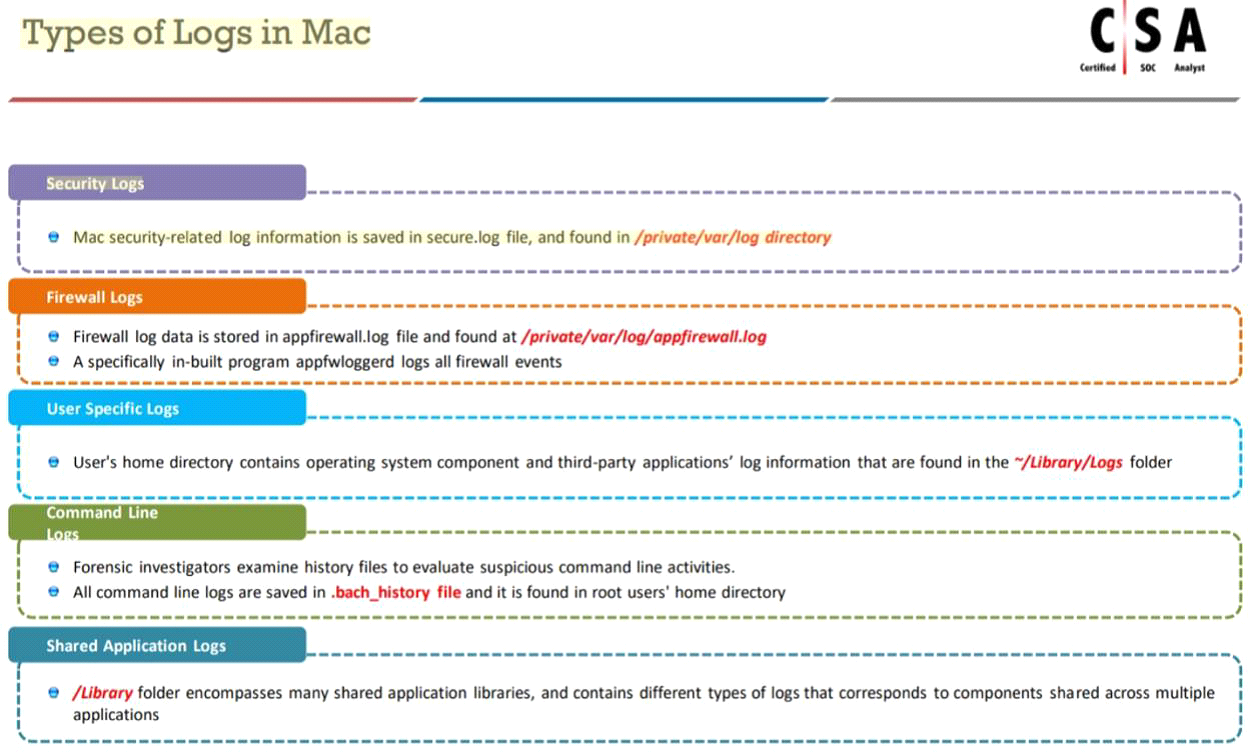
Which of the following is a default directory in a Mac OS X that stores security-related logs?
Correct : A
Start a Discussions
Which of the following attack can be eradicated by converting all non-alphanumeric characters to HTML character entities before displaying the user input in search engines and forums?
Correct : C
Start a Discussions