Master CompTIA PT0-003 Exam with Reliable Practice Questions
A penetration tester obtains password dumps associated with the target and identifies strict lockout policies. The tester does not want to lock out accounts when attempting access. Which of the following techniques should the tester use?
Correct : A
To avoid locking out accounts while attempting access, the penetration tester should use credential stuffing.
Credential Stuffing:
Definition: An attack method where attackers use a list of known username and password pairs, typically obtained from previous data breaches, to gain unauthorized access to accounts.
Advantages: Unlike brute-force attacks, credential stuffing uses already known credentials, which reduces the number of attempts per account and minimizes the risk of triggering account lockout mechanisms.
Tool: Tools like Sentry MBA, Snipr, and others are commonly used for credential stuffing attacks.
Other Techniques:
MFA Fatigue: A social engineering tactic to exhaust users into accepting multi-factor authentication requests, not applicable for avoiding lockouts in this context.
Dictionary Attack: Similar to brute-force but uses a list of likely passwords; still risks lockout due to multiple attempts.
Brute-force Attack: Systematically attempts all possible password combinations, likely to trigger account lockouts due to high number of failed attempts.
Pentest Reference:
Password Attacks: Understanding different types of password attacks and their implications on account security.
Account Lockout Policies: Awareness of how lockout mechanisms work and strategies to avoid triggering them during penetration tests.
By using credential stuffing, the penetration tester can attempt to gain access using known credentials without triggering account lockout policies, ensuring a stealthier approach to password attacks.
Start a Discussions
A penetration tester runs a vulnerability scan that identifies several issues across numerous customer hosts. The executive report outlines the following information:
Server High-severity vulnerabilities
1. Development sandbox server 32
2. Back office file transfer server 51
3. Perimeter network web server 14
4. Developer QA server 92
The client is concerned about the availability of its consumer-facing production application. Which of the following hosts should the penetration tester select for additional manual testing?
Correct : C
Client Concern:
Availability: The client is specifically concerned about the availability of their consumer-facing production application. Ensuring this application is secure and available is crucial to the business.
Server Analysis:
Server 1 (Development sandbox server): Typically not a production server; vulnerabilities here are less likely to impact the consumer-facing application.
Server 2 (Back office file transfer server): Important but generally more internal-facing and less likely to directly affect the consumer-facing application.
Server 3 (Perimeter network web server): Likely hosts the consumer-facing application or critical services related to it. High-severity vulnerabilities here could directly impact availability.
Server 4 (Developer QA server): Similar to Server 1, more likely to be used for testing rather than production, making it less critical for immediate manual testing.
Pentest Reference:
Risk Prioritization: Focus on assets that have the most significant impact on business operations, especially those directly facing consumers.
Critical Infrastructure: Ensuring the security and availability of web servers exposed to the internet as they are prime targets for attacks.
By selecting Server 3 (the perimeter network web server) for additional manual testing, the penetration tester addresses the client's primary concern about the availability and security of the consumer-facing production application.
Start a Discussions
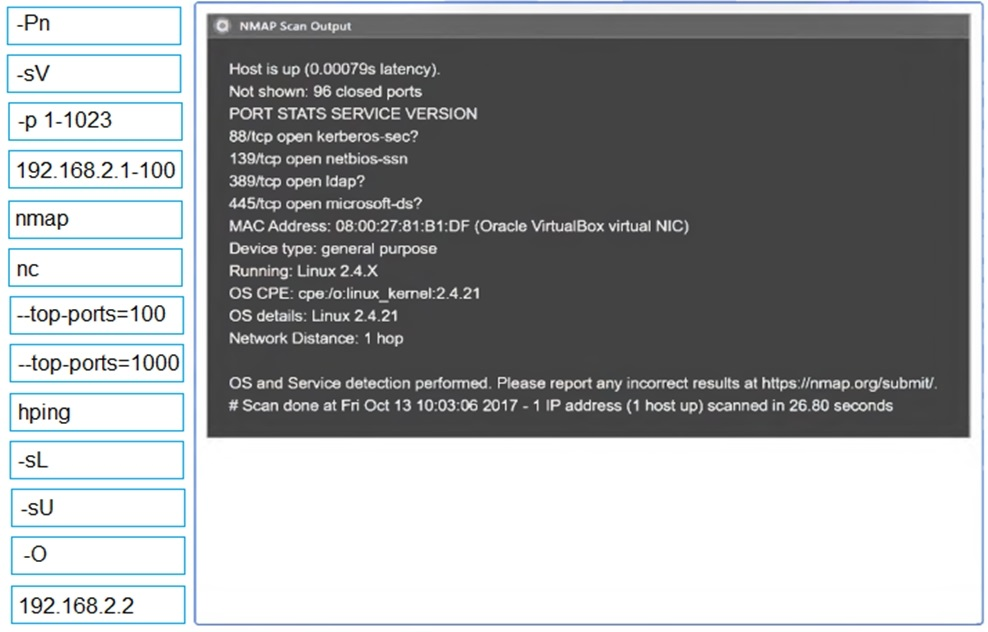
SIMULATION
You are a penetration tester running port scans on a server.
INSTRUCTIONS
Part 1: Given the output, construct the command that was used to generate this output from the available options.
Part 2: Once the command is appropriately constructed, use the given output to identify the potential attack vectors that should be investigated further.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
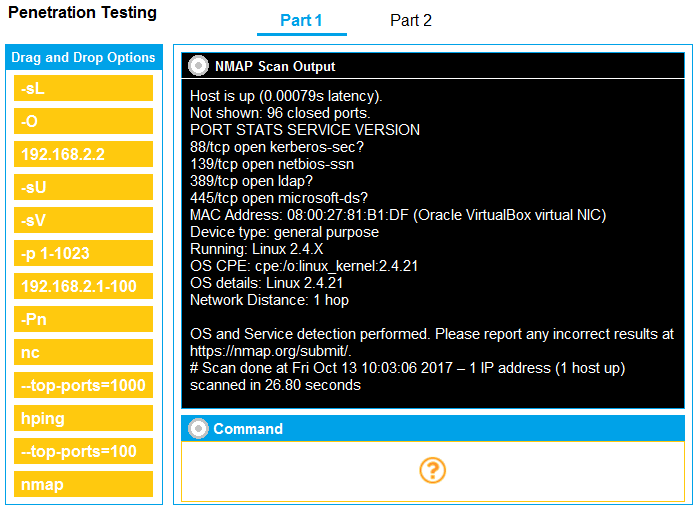
Correct : A
Part 1 - 192.168.2.2 -O -sV --top-ports=100 and SMB vulns
Part 2 - Weak SMB file permissions
Start a Discussions
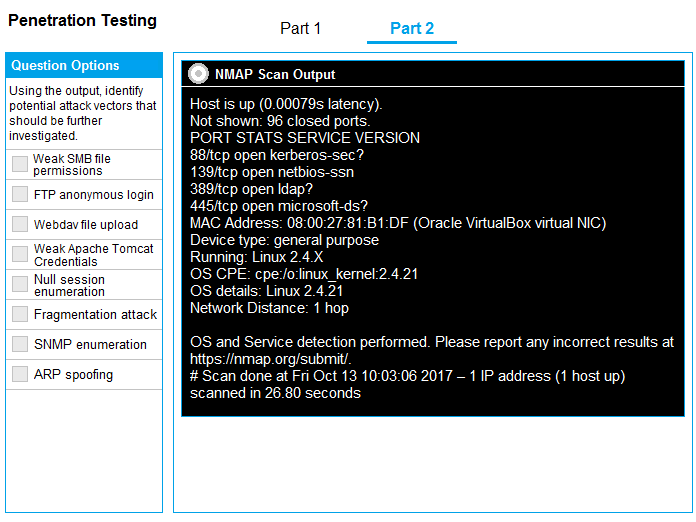
SIMULATION
Using the output, identify potential attack vectors that should be further investigated.
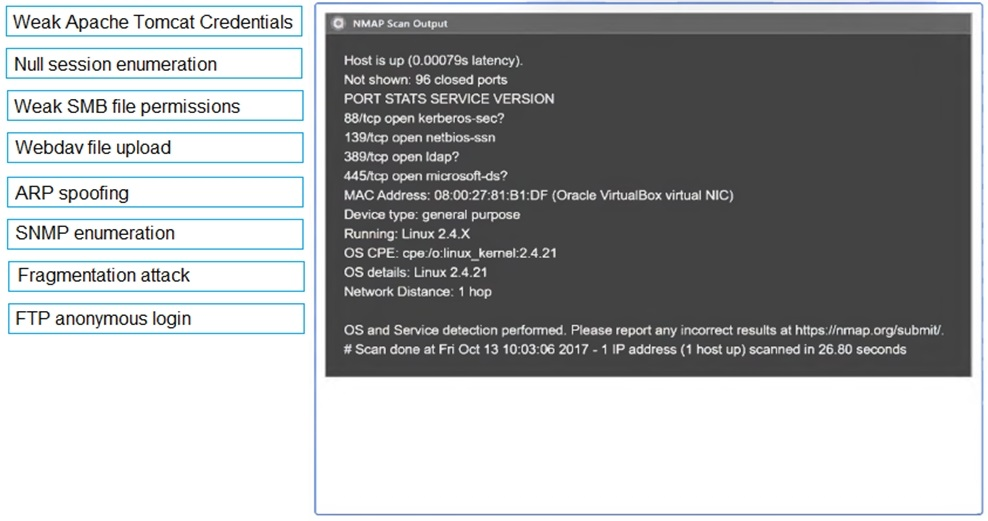
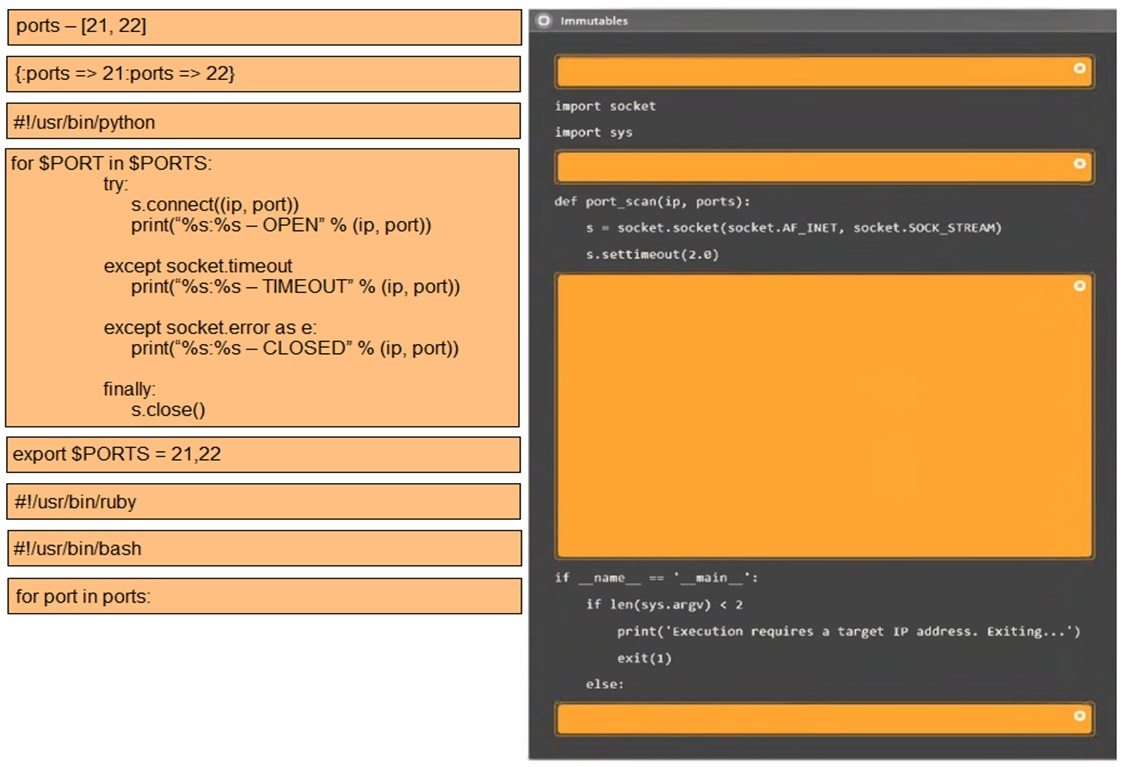
Correct : A
1: Null session enumeration
Weak SMB file permissions
Fragmentation attack
2: nmap
-sV
-p 1-1023
192.168.2.2
3: #!/usr/bin/python
export $PORTS = 21,22
for $PORT in $PORTS:
try:
s.connect((ip, port))
print(''%s:%s -- OPEN'' % (ip, port))
except socket.timeout
print(''%:%s -- TIMEOUT'' % (ip, port))
except socket.error as e:
print(''%:%s -- CLOSED'' % (ip, port))
finally
s.close()
port_scan(sys.argv[1], ports)
Start a Discussions
A penetration tester is conducting reconnaissance on a target network. The tester runs the following Nmap command: nmap -sv -sT -p - 192.168.1.0/24. Which of the following describes the most likely purpose of this scan?
Correct : C
The Nmap command nmap -sv -sT -p- 192.168.1.0/24 is designed to discover services on a network. Here is a breakdown of the command and its purpose:
Command Breakdown:
nmap: The network scanning tool.
-sV: Enables service version detection. This option tells Nmap to determine the version of the services running on open ports.
-sT: Performs a TCP connect scan. This is a more reliable method of scanning as it completes the TCP handshake but can be easily detected by firewalls and intrusion detection systems.
-p-: Scans all 65535 ports. This ensures a comprehensive scan of all possible TCP ports.
192.168.1.0/24: Specifies the target network range (subnet) to be scanned.
Purpose of the Scan:
Service Discovery (Answer: C): The primary purpose of this scan is to discover
Service discovery is a common task in penetration testing to map out the network services and versions, as seen in various Hack The Box (HTB) write-ups where comprehensive service enumeration is performed before further actions.
Conclusion: The nmap -sv -sT -p- 192.168.1.0/24 command is most likely used for service discovery, as it aims to identify all running services and their versions on the target subnet.
Start a Discussions