Master CompTIA CAS-005 Exam with Reliable Practice Questions
Asecuntv administrator is performing a gap assessment against a specific OS benchmark The benchmark requires the following configurations be applied to endpomts:
* Full disk encryption
* Host-based firewall
* Time synchronization
* Password policies
* Application allow listing
* Zero Trust application access
Which of the following solutions best addresses the requirements? (Select two).
Correct : C, D
To address the specific OS benchmark configurations, the following solutions are most appropriate:
C . SCAP (Security Content Automation Protocol): SCAP helps in automating vulnerability management and policy compliance, including configurations like full disk encryption, host-based firewalls, and password policies.
D . SASE (Secure Access Service Edge): SASE provides a framework for Zero Trust network access and application allow listing, ensuring secure and compliant access to applications and data.
These solutions together cover the comprehensive security requirements specified in the OS benchmark, ensuring a robust security posture for endpoints.
CompTIA SecurityX Study Guide: Discusses SCAP and SASE as part of security configuration management and Zero Trust architectures.
NIST Special Publication 800-126, 'The Technical Specification for the Security Content Automation Protocol (SCAP)': Details SCAP's role in security automation.
'Zero Trust Networks: Building Secure Systems in Untrusted Networks' by Evan Gilman and Doug Barth: Covers the principles of Zero Trust and how SASE can implement them.
By implementing SCAP and SASE, the organization ensures that all the specified security configurations are applied and maintained effectively.
Start a Discussions
After an incident response exercise, a security administrator reviews the following table:
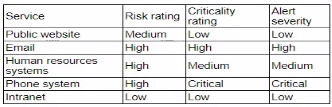
Which of the following should the administrator do to beat support rapid incident response in the future?
Correct : B
Enabling dashboards for service status monitoring is the best action to support rapid incident response. The table shows various services with different risk, criticality, and alert severity ratings. To ensure timely and effective incident response, real-time visibility into the status of these services is crucial.
Why Dashboards for Service Status Monitoring?
Real-time Visibility: Dashboards provide an at-a-glance view of the current status of all critical services, enabling rapid detection of issues.
Centralized Monitoring: A single platform to monitor the status of multiple services helps streamline incident response efforts.
Proactive Alerting: Dashboards can be configured to show alerts and anomalies immediately, ensuring that incidents are addressed as soon as they arise.
Improved Decision Making: Real-time data helps incident response teams make informed decisions quickly, reducing downtime and mitigating impact.
Other options, while useful, do not offer the same level of comprehensive, real-time visibility and proactive alerting:
A . Automate alerting to IT support for phone system outages: This addresses one service but does not provide a holistic view.
C . Send emails for failed log-in attempts on the public website: This is a specific alert for one type of issue and does not cover all services.
D . Configure automated isolation of human resources systems: This is a reactive measure for a specific service and does not provide real-time status monitoring.
CompTIA SecurityX Study Guide
NIST Special Publication 800-61 Revision 2, 'Computer Security Incident Handling Guide'
'Best Practices for Implementing Dashboards,' Gartner Research
Start a Discussions
Company A and Company D ate merging Company A's compliance reports indicate branch protections are not in place A security analyst needs to ensure that potential threats to the software development life cycle are addressed. Which of the following should me analyst cons
Correct : C
Dynamic Application Security Testing (DAST) is crucial for identifying and addressing security vulnerabilities during the software development life cycle (SDLC). Ensuring that DAST scans are routinely scheduled helps in maintaining a secure development process.
Why Routine DAST Scans?
Continuous Security Assessment: Regular DAST scans help in identifying vulnerabilities in real-time, ensuring they are addressed promptly.
Compliance: Routine scans ensure that the development process complies with security standards and regulations.
Proactive Threat Mitigation: Regular scans help in early detection and mitigation of potential security threats, reducing the risk of breaches.
Integration into SDLC: Ensures security is embedded within the development process, promoting a security-first approach.
Other options, while relevant, do not directly address the continuous assessment and proactive identification of threats:
A . If developers are unable to promote to production: This is more of an operational issue than a security assessment.
B . If DAST code is being stored to a single code repository: This concerns code management rather than security testing frequency.
D . If role-based training is deployed: While important, training alone does not ensure continuous security assessment.
CompTIA SecurityX Study Guide
OWASP Testing Guide
NIST Special Publication 800-53, 'Security and Privacy Controls for Information Systems and Organizations'
Start a Discussions
A security analyst discovered requests associated with IP addresses known for born legitimate 3nd bot-related traffic. Which of the following should the analyst use to determine whether the requests are malicious?
Correct : A
The user-agent string can provide valuable information to distinguish between legitimate and bot-related traffic. It contains details about the browser, device, and sometimes the operating system of the client making the request.
Why Use User-Agent String?
Identify Patterns: User-agent strings can help identify patterns that are typical of bots or legitimate users.
Block Malicious Bots: Many bots use known user-agent strings, and identifying these can help block malicious requests.
Anomalies Detection: Anomalous user-agent strings can indicate spoofing attempts or malicious activity.
Other options provide useful information but may not be as effective for initial determination of the nature of the request:
B . Byte length of the request: This can indicate anomalies but does not provide detailed information about the client.
C . Web application headers: While useful, they may not provide enough distinction between legitimate and bot traffic.
D . HTML encoding field: This is not typically used for identifying the nature of the request.
CompTIA SecurityX Study Guide
'User-Agent Analysis for Security,' OWASP
NIST Special Publication 800-94, 'Guide to Intrusion Detection and Prevention Systems (IDPS)'
Start a Discussions
An organization is required to
* Respond to internal and external inquiries in a timely manner
* Provide transparency.
* Comply with regulatory requirements
The organization has not experienced any reportable breaches but wants to be prepared if a breach occurs in the future. Which of the following is the best way for the organization to prepare?
Correct : C
Preparing communication templates that have been vetted by both internal and external counsel ensures that the organization can respond quickly and effectively to internal and external inquiries, comply with regulatory requirements, and provide transparency in the event of a breach.
Why Communication Templates?
Timely Response: Pre-prepared templates ensure that responses are ready to be deployed quickly, reducing response time.
Regulatory Compliance: Templates vetted by counsel ensure that all communications meet legal and regulatory requirements.
Consistent Messaging: Ensures that all responses are consistent, clear, and accurate, maintaining the organization's credibility.
Crisis Management: Pre-prepared templates are a critical component of a broader crisis management plan, ensuring that all stakeholders are informed appropriately.
Other options, while useful, do not provide the same level of preparedness and compliance:
A . Outsourcing to an external consultant: This may delay response times and lose internal control over the communication.
B . Integrating automated response mechanisms: Useful for efficiency but not for ensuring compliant and vetted responses.
D . Conducting lessons-learned activities: Important for improving processes but does not provide immediate preparedness for communication.
CompTIA SecurityX Study Guide
NIST Special Publication 800-61 Revision 2, 'Computer Security Incident Handling Guide'
ISO/IEC 27002:2013, 'Information technology --- Security techniques --- Code of practice for information security controls'
Start a Discussions