Master Cisco 350-201 Exam with Reliable Practice Questions
A security engineer discovers that a spreadsheet containing confidential information for nine of their employees was fraudulently posted on a competitor's website. The spreadsheet contains names, salaries, and social security numbers. What is the next step the engineer should take in this investigation?
Correct : D
Start a Discussions
Refer to the exhibit.
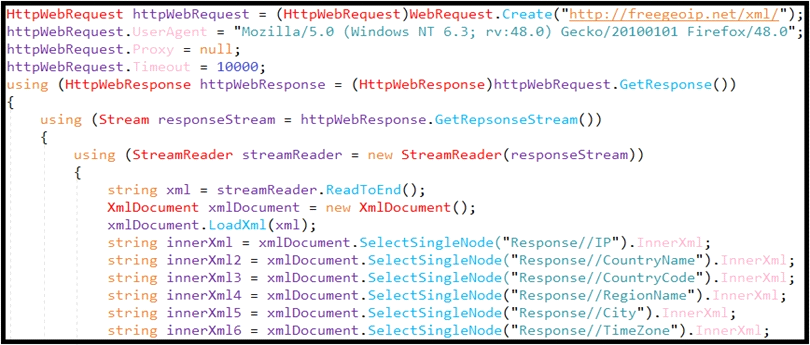
An engineer is performing static analysis of a file received and reported by a user. Which risk is indicated in this STIX?
Correct : D
Start a Discussions
A SOC team receives multiple alerts by a rule that detects requests to malicious URLs and informs the incident response team to block the malicious URLs requested on the firewall. Which action will improve the effectiveness of the process?
Correct : A
Start a Discussions
A cloud engineer needs a solution to deploy applications on a cloud without being able to manage and control the server OS. Which type of cloud environment should be used?
Correct : A
Start a Discussions
An analyst received multiple alerts on the SIEM console of users that are navigating to malicious URLs. The analyst needs to automate the task of receiving alerts and processing the data for further investigations. Three variables are available from the SIEM console to include in an automation script: console_ip, api_token, and reference_set_name. What must be added to this script to receive a successful HTTP response?
#!/usr/bin/python import sys import requests
Correct : C
Start a Discussions