Master Cisco 300-440 Exam with Reliable Practice Questions
Refer to the exhibits.
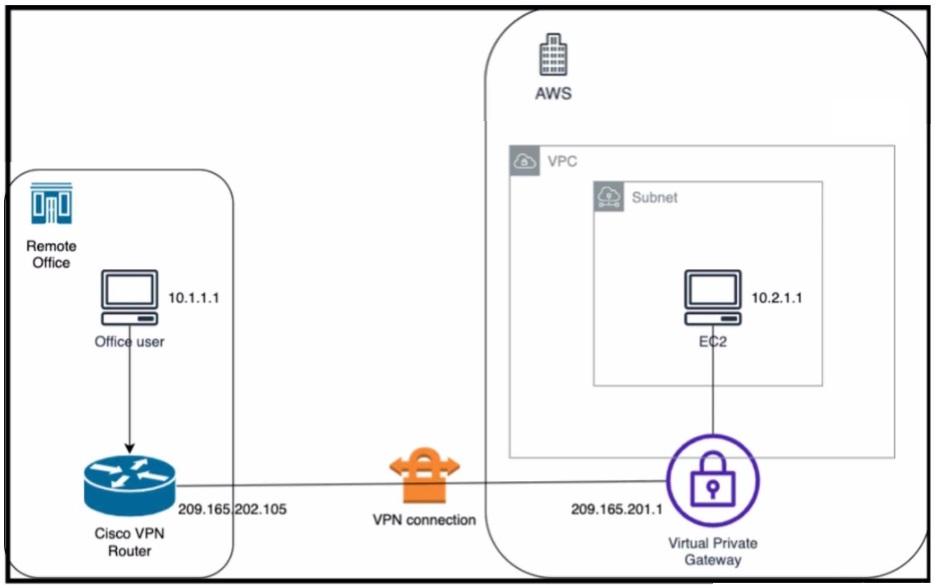
Refer to the exhibit. An engineer successfully brings up the site-to-site VPN tunnel between the remote office and the AWS virtual private gateway, and the site-to-site routing works correctly. However, the end-to-end ping between the office user PC and the AWS EC2 instance is not working. Which two actions diagnose the loss of connectivity? (Choose two.)
Correct : B, C
The end-to-end ping between the office user PC and the AWS EC2 instance is not working because either the security group rules for the host VPC are blocking the ICMP traffic or the IPsec SA counters are showing errors or drops. To diagnose the loss of connectivity, the engineer should check both the security group rules and the IPsec SA counters. The network security group rules on the host VNET are not relevant because they apply to Azure, not AWS. The IPsec SA configuration on the Cisco VPN router and the AWS private virtual gateway are not likely to be the cause of the problem because the site-to-site VPN tunnel is already up and the site-to-site routing works correctly.Reference:=
AWS Documentation, User Guide for AWS VPN, Section: Security Groups for Your VPC
Start a Discussions
Refer to the exhibit.
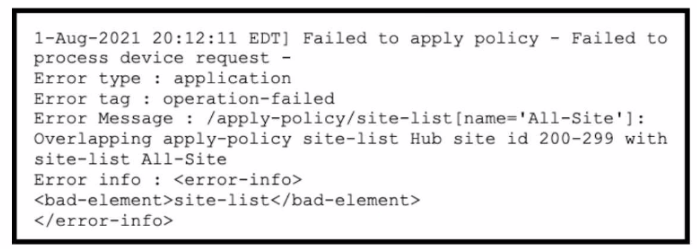
A company uses Cisco SD-WAN in the data center. All devices have the default configuration. An engineer attempts to add a new centralized control policy in Cisco vManage but receives an error message. What is the problem?
Correct : D
The problem is that the site-list ''All-Site'' has a higher match sequence than the site-list ''Hub'', which means that the policy for ''All-Site'' will take precedence over the policy for ''Hub'' for any site that belongs to both lists. This creates a conflict and prevents the engineer from adding a new centralized control policy in Cisco vManage. To resolve this issue, the site-list ''All-Site'' should be configured with a new match sequence that is lower than the sequence for site-list ''Hub'', so that the policy for ''Hub'' will be applied first and then the policy for ''All-Site'' will be applied only to the remaining sites that are not in the ''Hub'' list.Reference:=
Start a Discussions
A company with multiple branch offices wants a suitable connectivity model to meet these network architecture requirements:
* high availability
* quality of service (QoS)
* multihoming
* specific routing needs
Which connectivity model meets these requirements?
Correct : D
A fully meshed topology with SD-WAN technology using dynamic routing and prioritized traffic for QoS meets the network architecture requirements of the company. A fully meshed topology provides high availability by eliminating single points of failure and allowing multiple paths between branch offices. SD-WAN technology enables multihoming by supporting multiple transport options, such as MPLS, internet, LTE, etc. SD-WAN also provides QoS by applying policies to prioritize traffic based on application, user, or network conditions. Dynamic routing allows the SD-WAN solution to adapt to changing network conditions and optimize the path selection for each traffic type. A fully meshed topology with SD-WAN technology can also support specific routing needs, such as segment routing, policy-based routing, or application-aware routing.Reference:
Designing and Implementing Cloud Connectivity (ENCC) v1.0
[Cisco SD-WAN Design Guide]
[Cisco SD-WAN Configuration Guide]
Start a Discussions
A company has multiple branch offices across different geographic locations and a centralized data center. The company plans to migrate Its critical business applications to the public cloud infrastructure that is hosted in Microsoft Azure. The company requires high availability, redundancy, and low latency for its business applications. Which connectivity model meets these requirements?
Correct : A
The connectivity model that meets the requirements of high availability, redundancy, and low latency for the company's business applications isExpressRoute with private peering using SDCI.
By using ExpressRoute with private peering and SDCI, the company can achieve the following benefits:
Start a Discussions
Which method is used to create authorization boundary diagrams (ABDs)?
Start a Discussions