Master Cisco 200-201 Exam with Reliable Practice Questions
Refer to the exhibit.
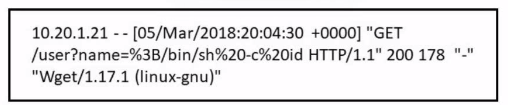
Which attack is being attempted against a web application?
Correct : C
The exhibit shows an HTTP GET request with a parameter that includes ; /bin/sh -c id.
This indicates a command injection attempt, where the attacker is trying to execute shell commands on the server.
Command injection vulnerabilities allow an attacker to execute arbitrary commands on the host operating system via a vulnerable application.
The use of /bin/sh and the -c flag is typical in command injection exploits to run shell commands, such as id, which returns user identity information.
OWASP Command Injection
Analyzing HTTP Requests for Injection Attacks
Web Application Security Testing Guidelines
Start a Discussions
A security engineer must investigate a recent breach within the organization. An engineer noticed that a breached workstation is trying to connect to the domain "Ranso4730-mware92-647". which is known as malicious. In which step of the Cyber Kill Chain is this event?
Correct : D
The event where a breached workstation is trying to connect to a known malicious domain suggests that the attacker is moving towards their end goals, which typically involves actions on objectives.
In the Cyber Kill Chain framework, 'Action on objectives' refers to the steps taken by an attacker to achieve their intended outcomes, such as data exfiltration, destruction, or ransom demands.
This phase involves the attacker executing their final mission within the target environment, leveraging access gained in earlier stages of the attack.
Lockheed Martin Cyber Kill Chain
Understanding the Stages of Cyber Attacks
Incident Response and the Cyber Kill Chain
Start a Discussions
What is data encapsulation?
Correct : B
Data encapsulation is a process in networking where the protocol stack of the sending host adds headers (and sometimes trailers) to the data.
Each layer of the OSI or TCP/IP model adds its own header to the data as it passes down the layers, preparing it for transmission over the network.
For example, in the TCP/IP model, data starts at the application layer and is encapsulated at each subsequent layer (Transport, Internet, and Network Access) before being transmitted.
This encapsulation ensures that the data is correctly formatted and routed to its destination, where the headers are stripped off in reverse order by the receiving host.
Networking Fundamentals by Cisco
OSI Model and Data Encapsulation Process
Understanding TCP/IP Encapsulation
Start a Discussions
Which type of attack uses a botnet to reflect requests off of an NTP server to overwhelm a target?
Correct : C
A Distributed Denial of Service (DDoS) attack involves multiple compromised devices (botnet) sending a large number of requests to a target server to overwhelm it.
In a specific type of DDoS attack known as an NTP amplification attack, the attacker exploits the Network Time Protocol (NTP) servers by sending small queries with a spoofed source IP address (the target's IP).
The NTP server responds with a much larger reply to the target's IP address, thereby amplifying the traffic directed at the target.
This reflection and amplification technique significantly increases the volume of traffic sent to the target, causing denial of service.
OWASP DDoS Attack Overview
NTP Amplification Attack Explained
Understanding Botnets and Distributed Attacks
Start a Discussions
Which of these is a defense-in-depth strategy principle?
Correct : C
Defense-in-depth is a layered security strategy that aims to protect information and resources through multiple security measures.
One of its key principles is the concept of least privilege, which means providing users and systems with the minimum level of access necessary to perform their job functions.
By assigning only the necessary permissions, the attack surface is reduced, and the potential damage from a compromised account or system is minimized.
This principle helps in mitigating the risk of unauthorized access and limits the capabilities of an attacker if they gain access to an account.
Defense-in-Depth Strategy by NIST
Principle of Least Privilege in Cybersecurity
Layered Security Approach Explained
Start a Discussions